Are you ready for a cyber attack?
Cybermap 360 can help you to be ready very quickly. At the same time, you’ll be compliant with most data protection laws!
%
Overall increase of malware in 2020
%
of breaches were linked to unpatched vulnerabilities
%
of breach victims were small to mid-sized businesses
- Quickly understand your cyber footprint
- Quickly protect your company against cyber risks
- Be compliant with data protection laws
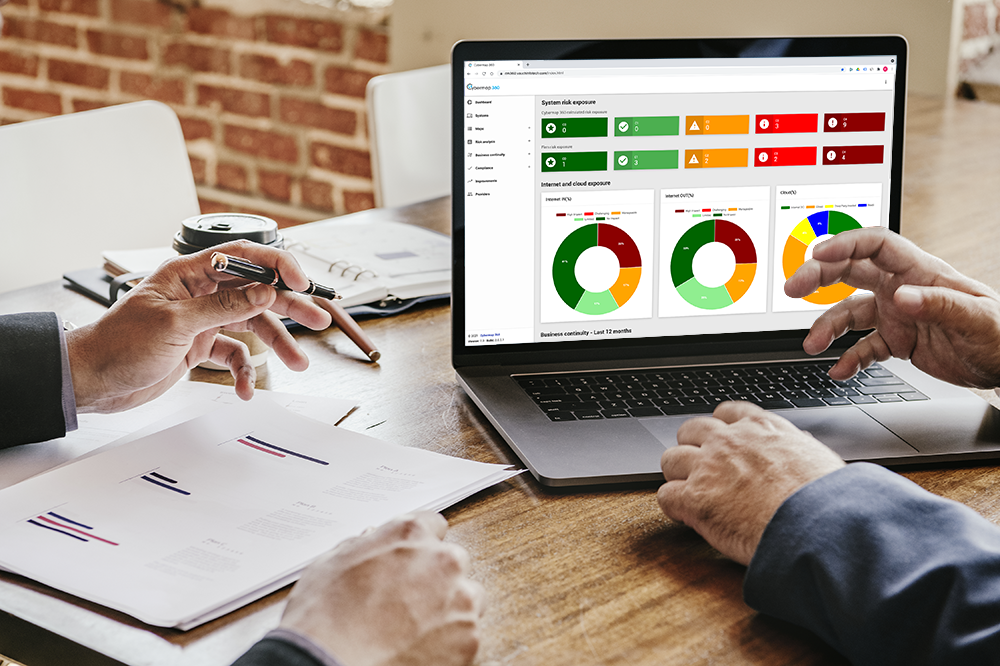
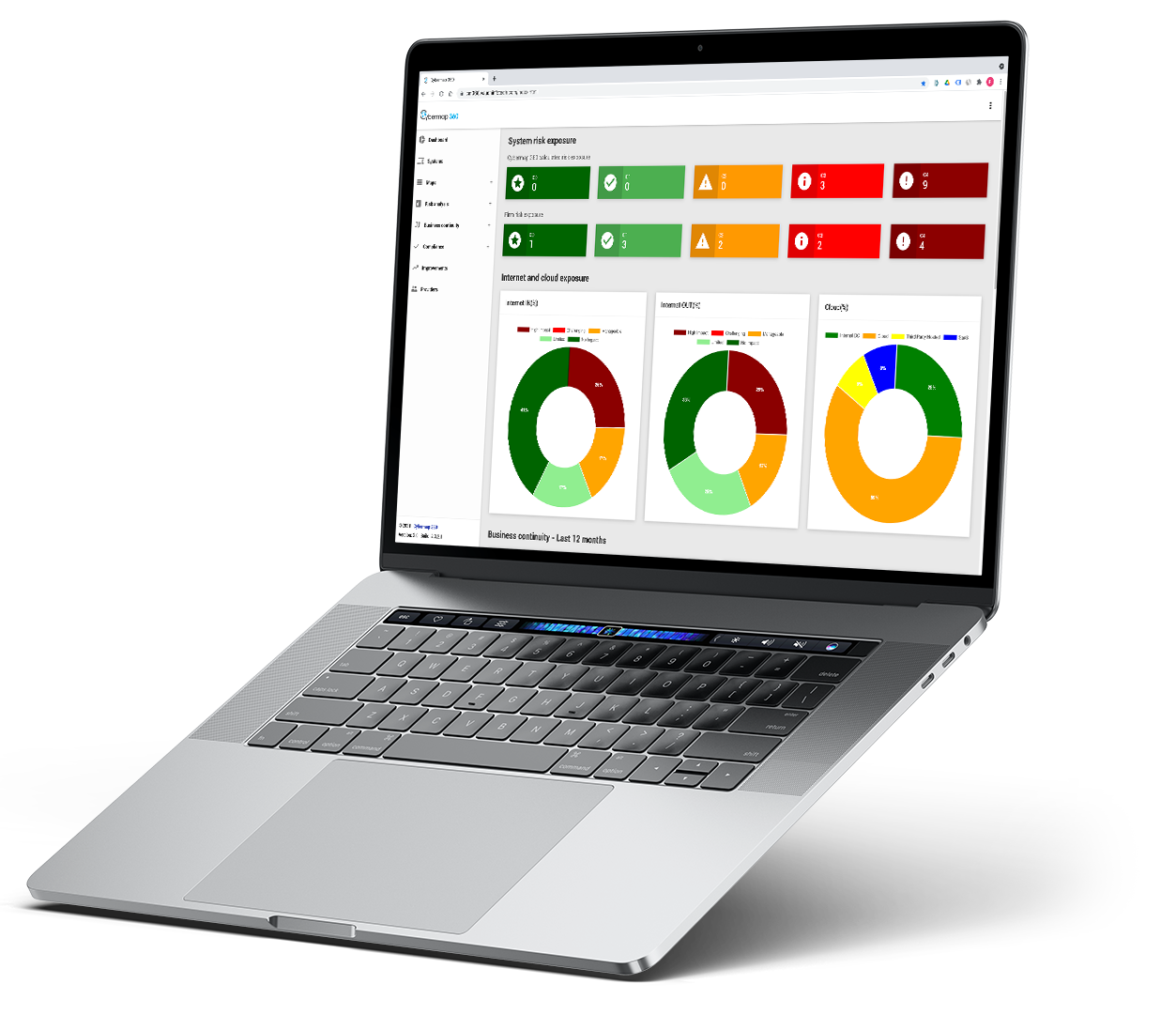
Understand and improve your cyber posture
Most small and mid-sized companies do not have an adequate view of their technology footprintYour digital footprint or cyber footprint is a picture of all the systems and data you have across the globe, whether this is on premises, with a third-party provider, or in the public cloud and its associated risks. System breaches can be devastating, destroy reputations, cost millions of dollars and wipe out a considerable portion of market capitalization.
Regulators have also demonstrated their appetites to pursue those who do not manage their cybersecurity and data confidentiality properly. Not to mention that executives are responsible for ensuring appropriate cybersecurity means and can quickly find themselves in a courtroom.
Our mission is to help small and mid-size companies to raise awareness about cybersecurity, understand their cybersecurity footprint and the associated cyber risks, and take appropriate actions to improve their cybersecurity posture. And to be ready for a future cyber incident. Because the question is not if it will happen but when it will happen? Are you ready for it?
Now with a new security checklist, customizable to fit your unique requirements. This tool is instrumental in deepening your understanding of your security posture and showcasing your compliance, particularly beneficial when facing audits or regulatory scrutiny.
Ensure you are compliant with data protection laws
All companies must have robust processes in place for handling and securely storing personal information. The processing of personal data must be adequate, relevant, and not excessive. This is not a “nice to have”, this is required by laws like the Swiss Data Protection Law and GDPR. The new version of Cybermap 360 fully supports you to ensure you are compliant with your legal obligations.
With Cybermap 360 you can comply with data protection laws by defining your processes, mapping your systems and data, understanding how data is shared with third parties, and if data is security managed in your systems.
A solution for both business and IT users
User-friendly
MORE INFOUser friendly
No need to be technical to use and leverage Cybermap 360. It has been designed for both Business and IT users.
Affordable
MORE INFOAffordable
Cybermap 360 runs in the cloud. No setting or maintenance fees. Just a yearly subscription that starts at CHF 500/year.
Business-driven
MORE INFOBusiness-driven
Engage your entire company in assessing and improving your cyber posture.
Move away from Excel-based inventories and assessments
FAQ
Here are some answers to Frequently Asked Questions about Cybermap 360.
What is a cyber footprint?
Your cyber footprint is a picture of all the systems and data you have across the globe, whether this is on-premises, with third-party providers, or in the cloud. Understanding your cyber footprint is the first step to have a solid cyber posture.
Is my business really exposed to cyber threats?
All companies, from all sectors and all sizes are exposed to cyber-attacks. A cyber-attack can make your information systems unusable, steal some trade secrets, steal your identity to commit other crimes, etc. It is estimated that cost of cybercrime has exceeded USD 1 trillion in 2020.
Does my company must protect its clients' data?
All companies, whatever size they have must comply with data protection laws like the Swiss Data Protection Law or GDPR. Some companies have been charged huge fines for not being compliant and not protecting the data of their clients appropriately.
What is included in the 30 days free access?
You will get full access to Cybermap 360, without any restrictions. Your trial period over, we can discuss the best way for you to continue using Cybermap 360.
Is Cybermap 360 secure?
Cybermap 360 is hosted in Switzerland, uses two-factor authentication, and encrypts all your data end-to-end, i.e., in transit and at rest. Cybermap 360 is a multi-tenant solution and your data is totally isolated from the data of other tenants. Cybermap 360 is not invasive, i.e., does not deploy any software within your IT infrastructure, and Cybermap 360 does not store any confidential data like usernames and passwords of your different systems.
Sources: 2019 Data Breach investigations Report, Digital resolve Small- and Mid-Sized Businesses Are Under Cyber AttackHelp Net Security – October 30, 2019 – Deep Instinct’s 2020 Cyber Threat Landscape report