MAP – ASSESS – IMPROVE
Improve your
cyber posture
Understand where your systems are and where your data is stored. Get some basics right in a very efficient and effective way

1 - MAP
Easily and simply map all your systems in Cybermap 360, and instantly understand in which countries your systems are and where your data is stored.

2 - ASSESS
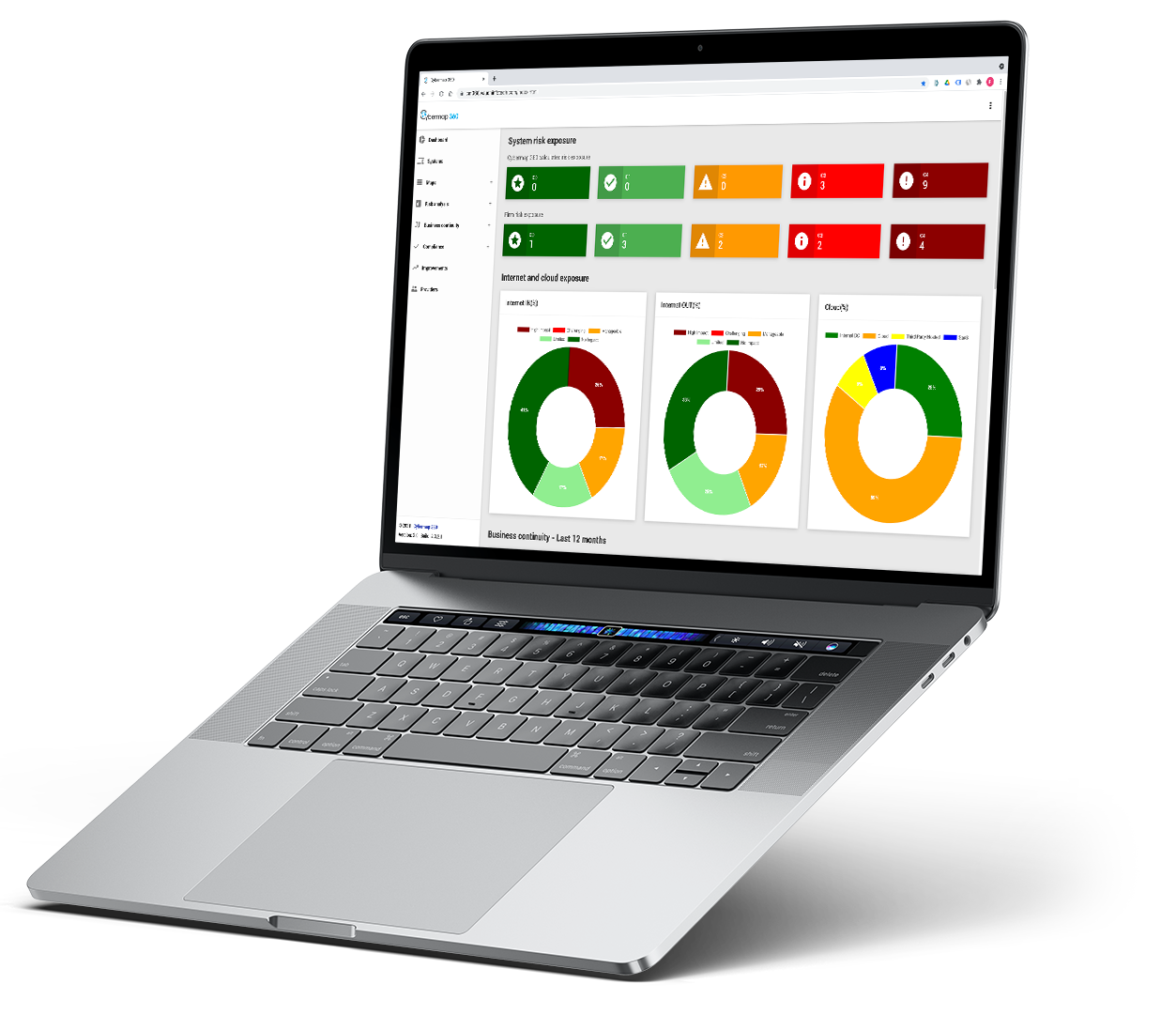
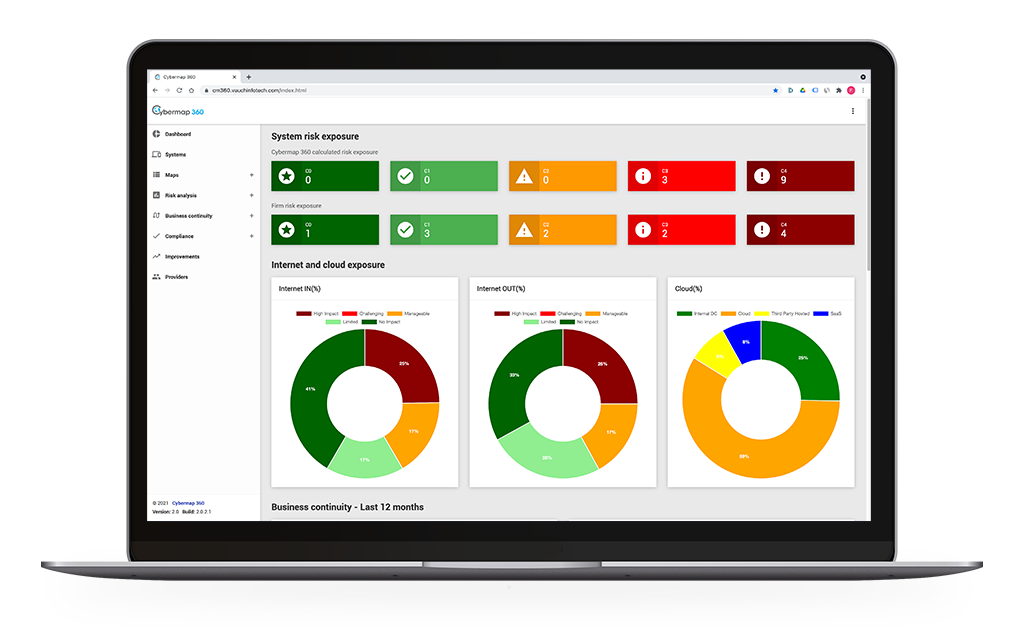
Immediately get your risk exposure for each system but also to the Cloud or the Internet. Get recommendations to improve your cyber posture.

3 - IMPROVE
Take appropriate actions to improve your cyber posture and be better prepared for a potential cyber-attack or incident.
Maintain an up-to-date view of your cyber footprint
Enter all your systems into Cybermap 360. For each system define its business criticality, data criticality, data it stores based on a pre-defined data map, hosting characteristics, business continuity readiness, and security parameters. More than 60 attributes can be captured by the system.
Understand your current risks
Identify factors that could impact your organization and make the most impactful, fact-based decisions.
The assessment has been divided into three categories to provide a more detailed evaluation of your standing:
Risk analysis
Evaluate your digital risk exposure.
Business continuity
Assess your business continuity and understand what needs to be done to improve your business continuity readiness.
Compliance
Assess your compliance to relevant regulations defined by your organization, or by external entities.
Improve your cyber posture
Based on Cybermap 360 recommendations, define improvement actions and actively track their implementation.
Benefits
Getting a strong cyber posture starts with some basics:
Mapping your cyber footprint, understanding the associated cyber risks, and taking appropriate actions.

BUSINESS-DRIVEN
Cybermap 360 does not require technical skills. It has been developed for business owners, board members, executive teams, compliance officers, and IT teams. It can be used across the entire organization.

Objective
Cybermap gives you an objective perspective of your cybersecurity posture, based on your cyber footprint and the setup of your different systems.

Distributed
Cybersecurity is the duty of the entire organization and with Cybermap 360 you can engage all players towards the same goal: improving your cybersecurity posture.

One thing only and NON-INVASIVE
Cybermap360 does one thing only and does not overlap with other cybersecurity solutions. Cybermap is non-invasive, i.e., it does not deploy software or agents within your network.
Features
All companies are exposed to cyber-attacks and cybersecurity has never been so important. Companies are exposed like never before!
Use Cybermap 360 to get an objective view of your cyber footprint and associated cyber risks.

SYSTEM Mapping
Enter all your systems into Cybermap 360. For each system define its business criticality, its data criticality, the data it stores based on a pre-defined data map, its hosting characteristics, its business continuity readiness, and its security parameters. There are more than 50 different parameters for each system, some mandatory, some optional. Cybermap360 uses industry-standard terminology.

Risks Analysis
Understand your exposure to the internet and what would happen if you would lose access. Understand your exposure to the public cloud and third-party providers’ infrastructures. Assess your compliance to relevant regulations defined by your organization, by entities. And much more.
Business Continuity
Assess your business continuity readiness using the system. Track your business continuity tests, whether tests have been successful, partially successful or failed. Understand what needs to be done to improve your business continuity readiness.

Systems’ risk assessment
Cybermap 360 calculates a risk rating for each system, with recommendations on how to improve this risk rating. As there is so much Cybermap360 knows about your systems, you can also define your own risk rating. Both are always visible, and you cannot override the risk rating calculated by Cybermap 360.

Improvement
Improve your cyber posture by defining improvement measures, with owners and due dates. Send reminders to improvements’ owners and continuously track how your cyber posture is improving (or deteriorating).

DATA PROTECTION
Comply with data protection laws by defining your business processes, linking your systems and the data used, ensuring data is properly and securely processed.
You will get a full access to Cybermap 360, without any restrictions. Your trial period over, we can discuss the best way for you to continue using Cybermap 360.