Contact us
Here is what you’re about to experience:
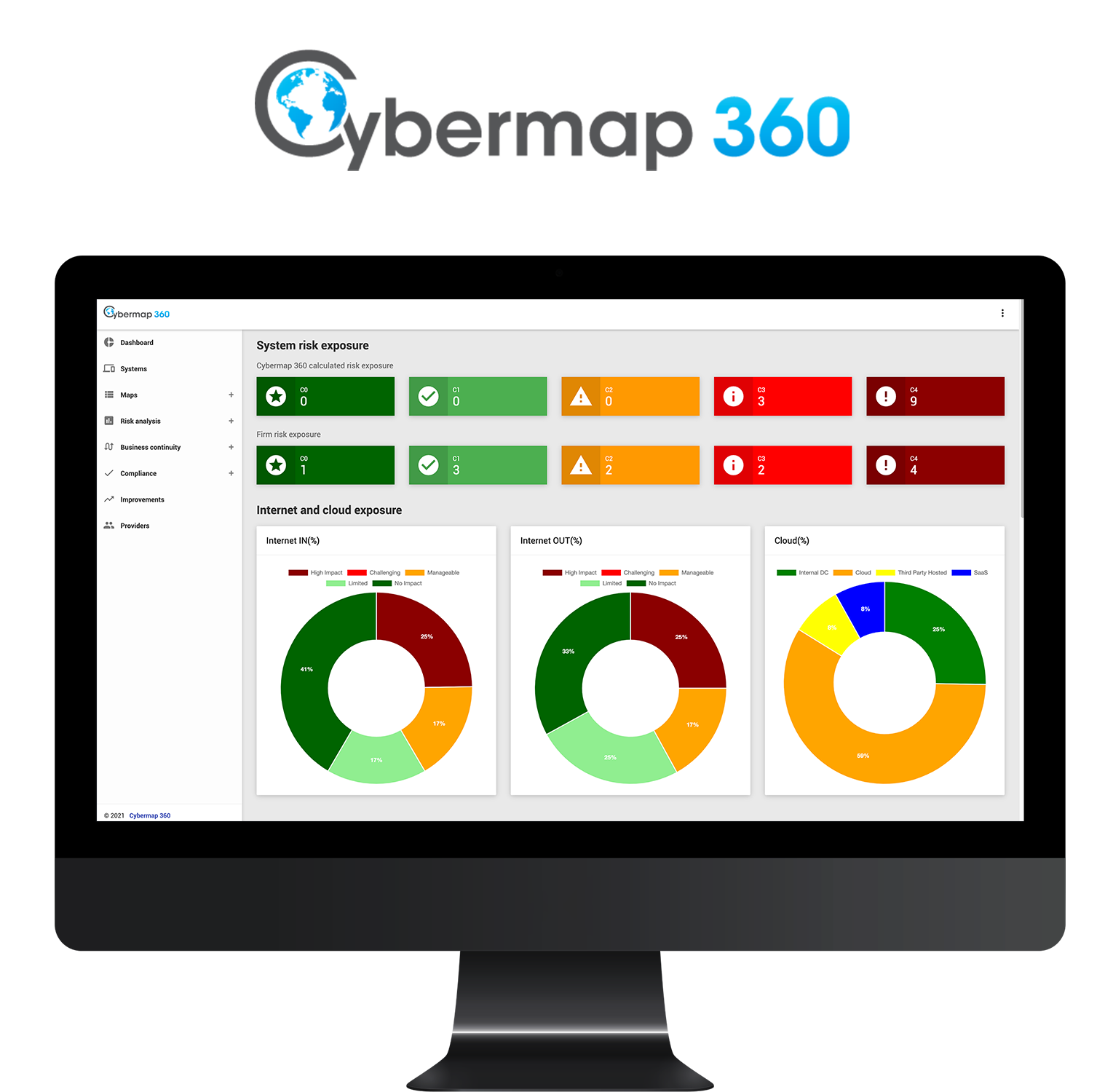
Easily map your systems and data, and get full visibility on your cyber footprint
Get an objective view of your cyber posture and vulnerabilities
Follow recommendations on how to improve your cyber posture and reduce risks
Understand your cloud and internet exposure
Ensure you are compliant with relevant regulations (e.g., GDPR)
Track how you progress in reducing cyber risks and improving your cyber posture
Engage all relevant people in this key activity, across your company, in one or multiple locations
Cybermap will only use your personal information for account administration of those products and services you’ve requested. By submitting your information, you agree to Cybermap’s Privacy Policy.
FAQ
Here are some answers to Frequently Asked Questions about Cybermap 360.
What is a cyber footprint?
Your cyber footprint is a picture of all the systems and data you have across the globe, whether this is on-premises, with third-party providers, or in the cloud. Understanding your cyber footprint is the first step to have a solid cyber posture.
Is my business really exposed to cyber threats?
All companies, from all sectors and all sizes are exposed to cyber-attacks. A cyber-attack can make your information systems unusable, steal some trade secrets, steal your identity to commit other crimes, etc. It is estimated that cost of cybercrime has exceeded USD 1 trillion in 2020.
What is included in the 30 days free access?
You will get full access to Cybermap 360, without any restrictions. Your trial period over, we can discuss the best way for you to continue using Cybermap 360.
Is Cybermap 360 secure?
Cybermap 360 is hosted in Switzerland, uses two-factor authentication, and encrypts all your data end-to-end, i.e., in transit and at rest. Cybermap 360 is a multi-tenant solution and your data is totally isolated from the data of other tenants. Cybermap 360 is not invasive, i.e., does not deploy any software within your IT infrastructure, and Cybermap 360 does not store any confidential data like usernames and passwords of your different systems.

